SINGAPORE: Phishing was likely used as a tool to gain access to a front-end computer at Singapore General Hospital, the Committee of Inquiry (COI) into the SingHealth cyberattack heard on Friday (Oct 5). The attacker then installed customised malware before laying dormant to execute their plan months later.
Forensic investigations found signs of call-backs to an overseas command and control server, said Solicitor-General Kwek Mean Luck as he presented a report by the Cyber Security Agency of Singapore (CSA) on the “modus operandi” of the cyber attackers. Such servers are used by attackers to talk to compromised computers within a target network.
The malware was “customised, uniquely tailored to the targeted systems, and had not been observed elsewhere”, the report said. The “skilful and technically advanced” attacker also used modified open-source tools that evaded anti-virus software, it added.
CSA said that the tools, techniques and procedures, as well as some of the malware that the attacker used fit the profile of an Advanced Persistent Threat (APT) group that it has previously encountered in other investigations.
READ: Singapore health system hit by ‘most serious breach of personal data’ in cyberattack; PM Lee’s data targeted
The cyberattack, which was Singapore’s most serious breach of public data to date, saw a total of 1.5 million patient records accessed and 160,000 records of outpatient dispensed medicine taken. Database administrators from the Integrated Health Information Systems (IHiS) – the central IT agency for the healthcare sector – discovered the breach on Jul 4 and acted immediately to stop it.
It also saw the personal particulars of Prime Minister Lee Hsien Loong, as well as information on his outpatient dispensed medicines, being “specifically and repeatedly” targeted.
KEY FACTORS THAT LED TO BREACH
According to the CSA report, there were three key factors which contributed to the cyberattack.
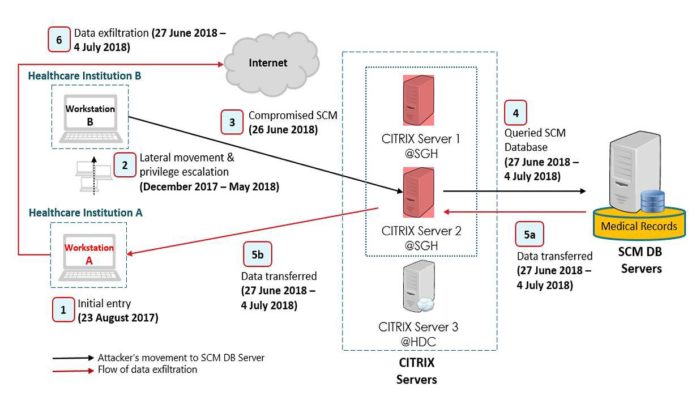
The first was the profile of the attacker, who was described as a “skilled and sophisticated threat actor” who used an “advanced modus operandi”, first gaining access on Aug 27 last year.
Utility tools such as Microsoft Powershell were likely to have been used alongside customised malware between steps two and three. (Photo: CSA)
The “stealthy and disciplined” attacker then laid low and only began exploiting the access after four months and moved in a “targeted manner” planning his route in the network between December 2017 and July 2018.
After compromising the initial computer, he proceeded to distribute malware and steal credentials, including user accounts and passwords including those that ultimately gave him access to the Electronic Medical Record (EMR) database.
“The attacker took care to avoid detection by moving quietly and slowly,” the report said.
“He avoided secondary targets that might have drawn attention to his presence. He was also careful and deliberate in erasing traces of his activities,” it added.
The attacker had also planted multiple footholds in the network, which was later used to attempt re-entry into the SingHealth system.
Secondly, weakness in SingHealth’s IT network allowed the attacker to gain access, said the report.
READ: Exploited server had not been updated for more than a year
The final reason identified by the report was a vulnerability in an application on the EMR database, which led to the breach.
READ: SingHealth COI hearing: Former IHiS CEO dismissed staff for ethical breach, didn’t probe alleged vulnerability
“From the evidence, it would appear to the COI, even at this stage, that the attacker had one and only one malicious intent, and that of exfiltrating data from the crown jewels of the network, which is EMR,” said COI chairman Richard Magnus in his closing remarks.
“I think at this stage the COI is inclined to accept the CSA’s assessment of the three factors that led to the cyber attack.”
CONTAINMENT MEASURES SUGGESTED BY CSA
After the breach was uncovered on Jul 4 and subsequently reported to CSA on Jul 10, IHiS and CSA implemented several immediate measures to contain the threat, eliminate the attacker’s foothold, and prevent the attack from recurring.
They include mandatory password changes for end-user computers which were completed on Jul 19 and Internet Surfing Separation policies, implemented on Jul 20, in view of call-backs to the overseas servers.
A master pass account, known as the Kerberos Golden Ticket, was also reset on Jul 12 twice to ensure that the attacker’s potential administrative privileges were invalidated.
The IHiS team also created firewall rules on Jul 13 to begin blocking malicious call-backs to identified overseas servers used by the attacker. Later on Jul 17, IHiS incorporated indicators that would help anti-virus systems recognise intrusions for system-wide scanning.
Citrix servers, which communicate between workstations and database servers were reloaded on Jul 14. Benign utility tools such as Microsoft PowerShell, which was used during the attack, was also disabled on Jul 13 on all end-user machines.
Over the past two weeks, the COI had heard from at least 14 witnesses at its public hearings ranging from former IHiS CEO Dr Chong Yoke Sin to assistant lead analyst Chai Sze Chun who went out of his way to investigate the hackings.
Part of the hearings was held behind closed doors, where evidence which involved national security matters were heard. For instance, the evidence may be exploited to carry out further cyber attacks or patients’ personal data may be revealed.
READ: COI for SingHealth cyberattacks: Officer took initiative to investigate even though it was not his job
Describing the Solicitor-General’s statement and the CSA’s investigation report as “essential” to the inquiry, Mr Magnus also added that both reports provided “clear insights into the modus operandi and the characteristics of the attacker”.
“As we all know, the COI is still ongoing, and I think we will consider all the evidence judiciously,” he added.
The inquiry will continue into its third tranche at end October. Witnesses are due to give evidence on areas such as the cybersecurity measures in place when the attack happened, the immediate responses to the cyberattack, IT governance frameworks as well as existing cybersecurity policies and their adequacy, Solicitor-General Kwek said.
The COI will hear from senior executives from IHiS and SingHealth, including IHiS’ director for cybersecurity governance Chua Kim Chuan, IHiS CEO Bruce Liang, and SingHealth Group CEO Ivy Ng, he added.
A report looking into the events and contributing factors leading to the cyber attack is due by end-2018.