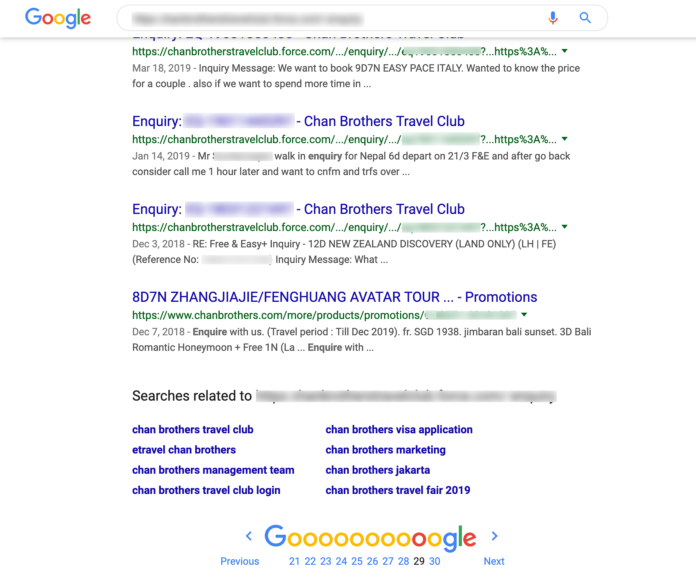
SINGAPORE: A security lapse on Chan Brothers’ website caused the personal data of its customers to be exposed, although the travel agency said “no sensitive booking and financial information was revealed”.
The vulnerability was discovered by Mr Andrew Goh, who works in the financial technology industry. He told CNA on Thursday (May 23) that because of the security flaw, he was able to see the booking records and enquiries made by Chan Brothers’ customers.
Mr Goh said he collected more than 500 customers’ personal details including names, email addresses, phone numbers and NRIC numbers as well as confidential corporate travel plans.
In an email to CNA on Friday, Chan Brothers confirmed the incident but said it “immediately” took action to contain the vulnerability and reported the incident to the Personal Data Protection Commission (PDPC).
It did not confirm the number of customers whose personal data was leaked.
SENSITIVE INFORMATION LISTED IN GOOGLE
Mr Goh said he stumbled on the security flaw while doing some research work.
He said he was trying to “scrape” user reviews to predict sales and bookings, and their possible effects on share prices, when he realised the Chan Brothers Travel Club webpage was “not properly configured” and the permission access was not set correctly.
He added that some sensitive administrator pages did not include a “noindex” tag, which meant Google would list those pages on its public search results.
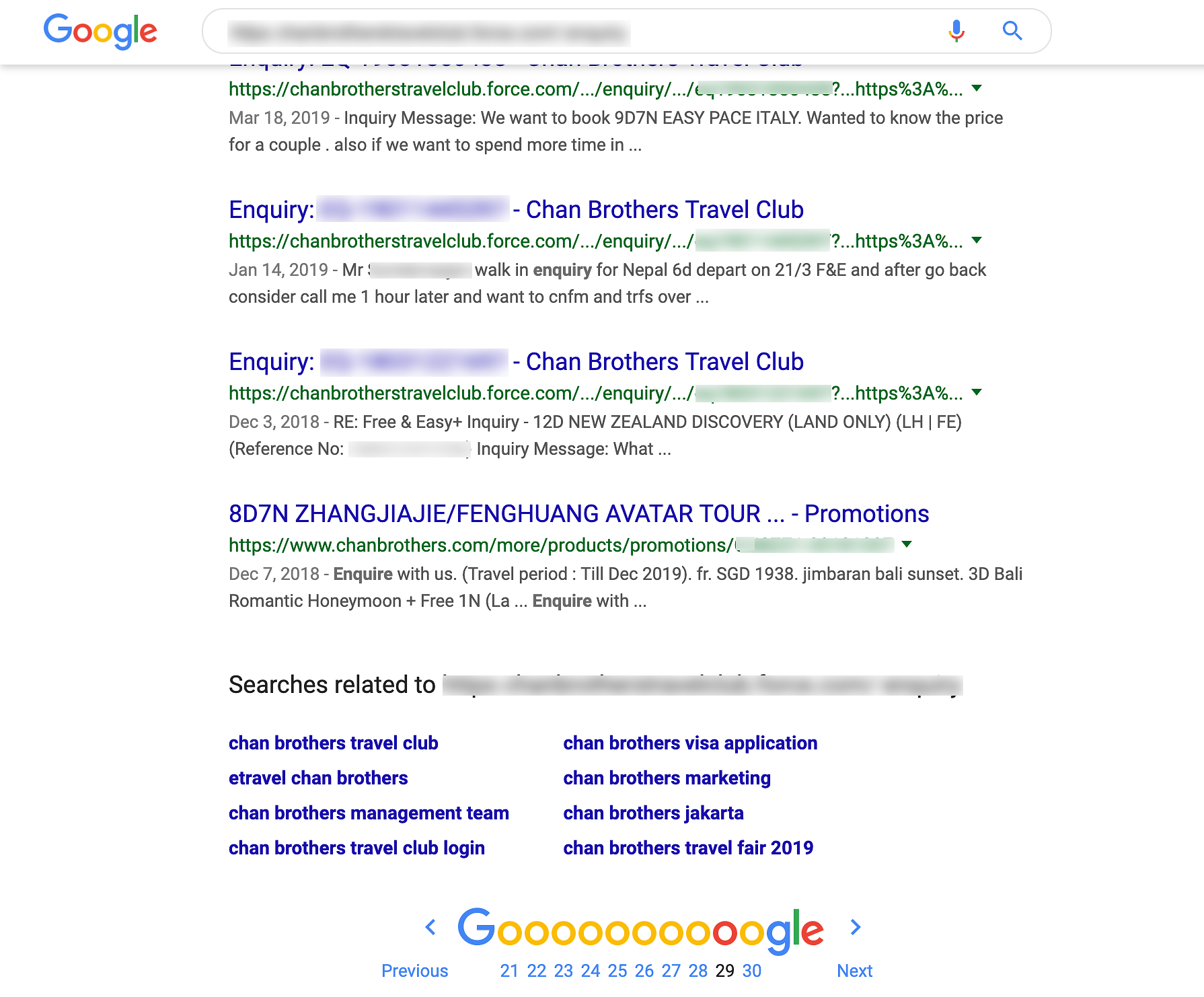
“Basically, the administrator of Chan Brothers governing the website and privileges did not enable password (protection) to the data,” he said, adding that he collected customer data from as far back as 2017.
In his email to CNA, Mr Goh shared a screengrab of an enquiry that appeared to be made by a Facebook employee asking for a quote for a “company incentive trip” scheduled for July.
After his discovery, Mr Goh contacted Chan Brothers on Thursday around noon to inform it of the vulnerability. In the email he sent to a Chan Brothers employee, and seen by CNA, he said the vulnerability “can cause potential breach of >500 of your customers”.
“I have tested and tried. A simple run of 1 hour yielded me more than 500 unique client data and they are very recent,” he wrote.
Mr Goh said an employee called him at about 1.20pm to inform him that “the issue has been resolved”. However, a check by him at 8.49pm found that the customer data could still be seen. He then sent a second email to Chan Brothers.
He said while the company put in a password prompt for anyone clicking on the URL links he had flagged, the information could still be seen through the cached pages.
CNA did its own check, and found that the information could still be seen as of 11.20pm on Thursday.
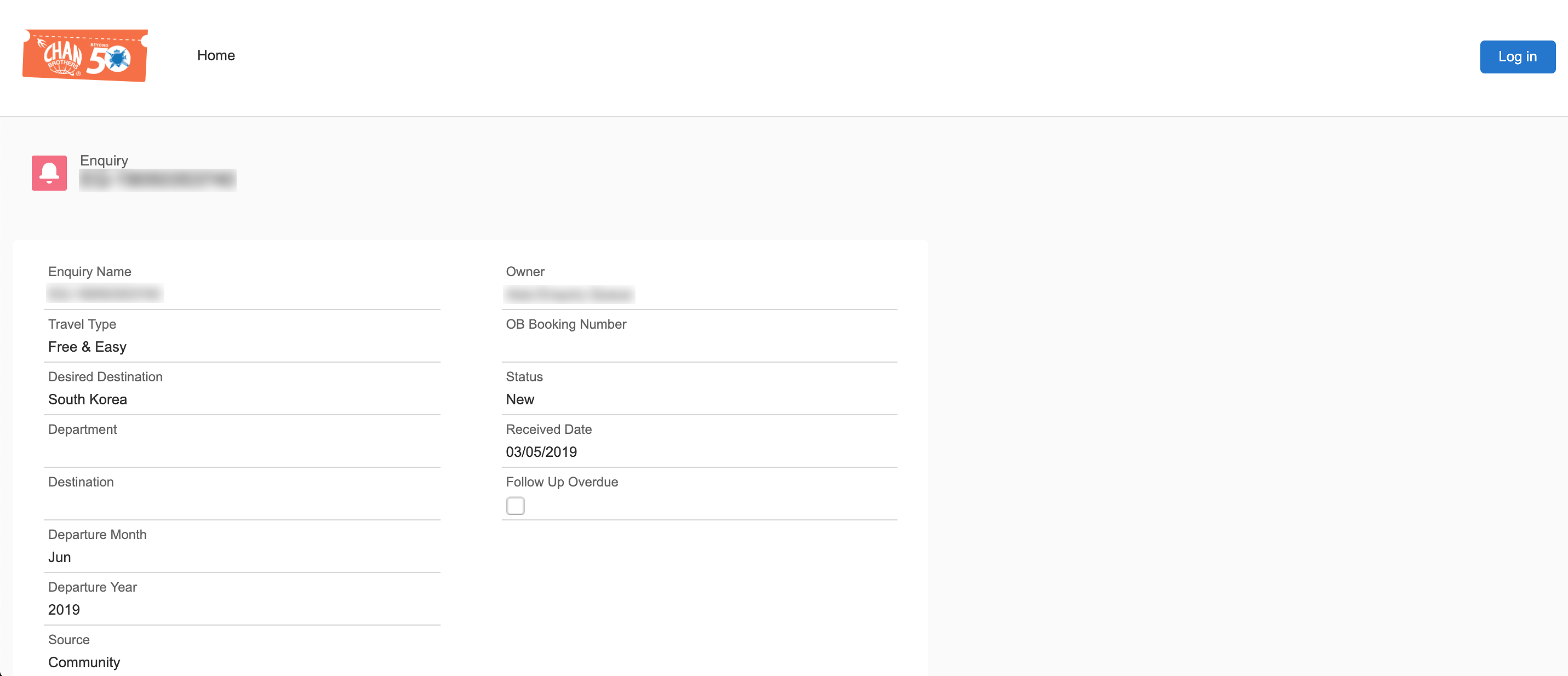
Chan Brothers’ head of marketing communications Jane Chang said the company is working with its vendor Aodigy Asia Pacific to investigate the incident and has instructed it to shut the site.
“We deeply regret that this occurred and take full responsibility for this incident,” Ms Chang said.
PDPC confirmed on Friday that it is investigating the incident.